Abstract
IoT security is important nowadays. The number of IoTs connected to the Internet is growing rapidly. IPS provides abilities of detecting and blocking malware packets. In addition to hardware IPSs, another approach is conducted by SDN with VNF technique which is deploying software (e.g., Zeek) in VM or server. However, existing SDN-based IPS methods have one big challenge “Long response time”.
P4-IPS: In-switch detecting and blocking malware
- Flow Filter : Match malware detection table to do action (e.g., forward, drop) or do feature extraction later.
- Feature Extractor : Mirror packets which built with self-defined headers and truncated payload to the control plane. ⇨ Forwarding pipeline offloading
- Malware Detector : Use multi-thread methods to parallelly detect packets with the neural network model and add entries to the table. ⇨ Reduce time of detecting packet
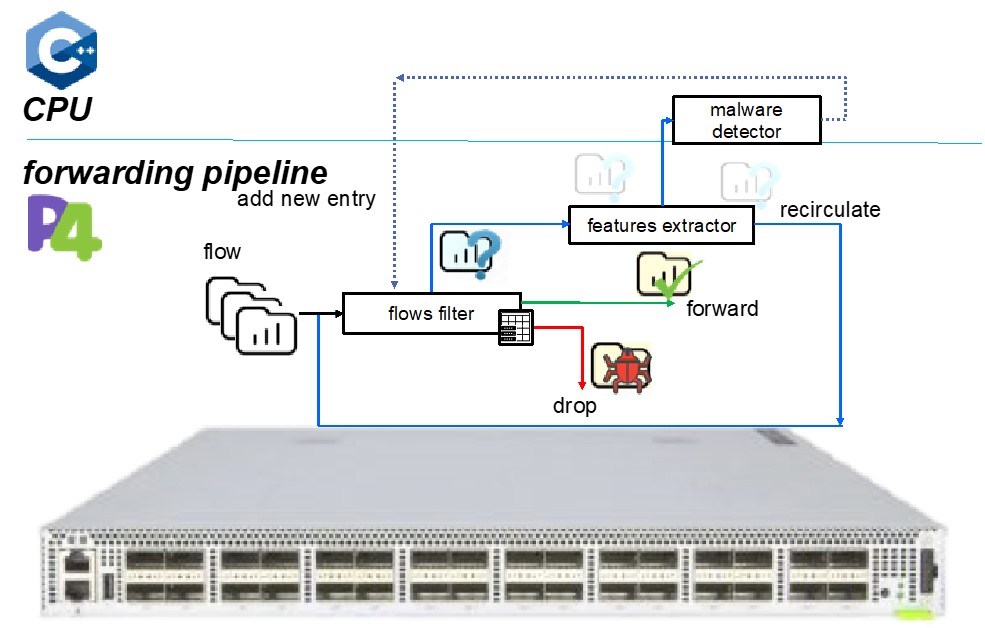
Fig. 1: P4-IPS Architecture
Environment setting
Host1 acts as sender which use ”tcpreplay” to send flows from the pcap file.
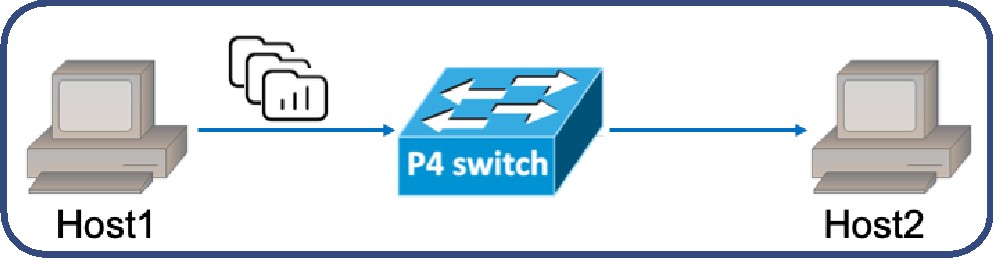
Fig. 2: Simple Test Environment
Evaluation
For Zeek, its processing capacity is less than 2 flows and response time is 119.63 ms.
Processing capacity (unit): single thread : 2950 flow/s and 8 threads : 9345 flow/s (4672x flows)
Average response time: single thread : 0.339 ms (352x faster)
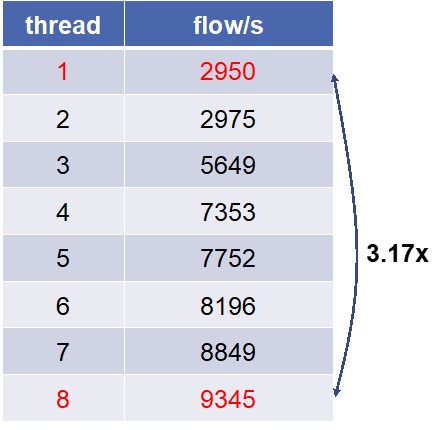
Fig. 3: Processing Capacity for Edgecore Wedge 100BF-32X