Abstract
Nowadays, when a user downloads a web page, many unwanted advertisements are embedded into the downloaded web page. To solve these problems, in this paper we design and implement a method inside a P4 hardware switch to block trackers and advertisements. Our method is to be deployed at a switch that connects an edge network to the Internet. Using such a configuration, all devices on the edge network will be automatically protected by our method without the need to install a per-device protection software.
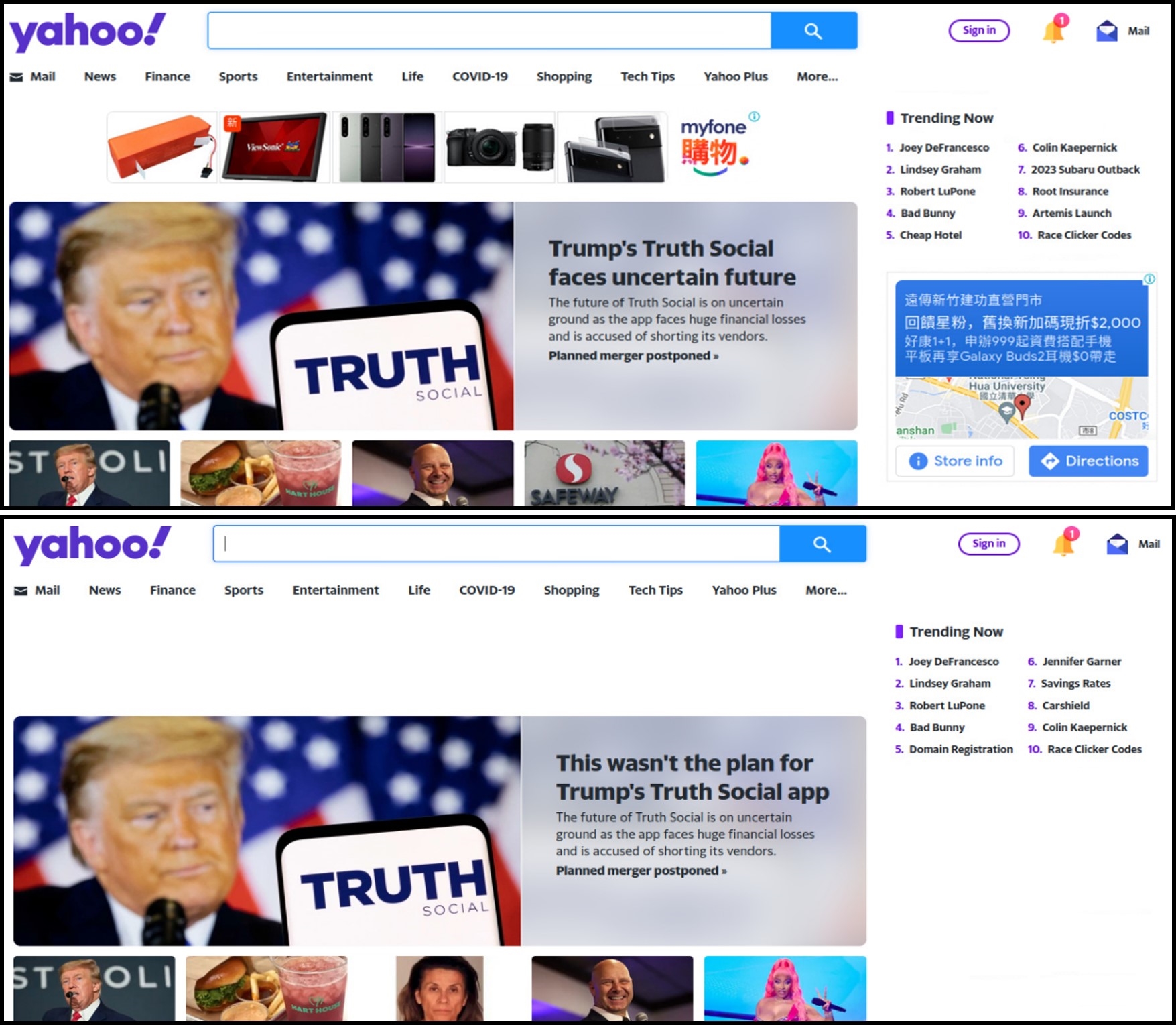
Fig. 1: Ads on the web page
Design and Implemtation
We use a P4 hardware switch to parse all DNS request packets passing through it. Furthermore, we import a filter list that contains lots of domain names related to trackers and advertisements. If the domain name carried in a DNS request packet is found to be on the filter list, our method will return 0.0.0.0 in the DNS reply packet as the resolved IP address for the queried domain name. Then, the HTTP requests of these domains will fail because of the invalid IP address.
Performance and Evaluation
We activated our method and observed its blocking effects on many commercial websites in this test. To clearly show its effectiveness, we selected Yahoo’s home page because it always displays many ads. Fig. 1 shows the difference between a web page with ads and without ads, respectively. This page was downloaded successfully without losing its original contents. The differences between the top and bottom pages are visible to naked eyes. Our method blocked the ads and thus caused the blank space at the top and bottom-right corner of the page.
We compared how much ads traffic can be blocked by “P4 ad blocker” when compared against the original traffic. We collected 34 websites for this test that contained many trackers and ads. Then, we wrote a Python script auto browse these websites repeatedly and recorded the difference of traffic with our method. The result shows in Fig. 2, “P4 ad blocker” can reduce the number of “All protocols” packets by 40.92% and reduce the number of TCP-only packets by 40.33%. We also compares the average number of “All protocols” bytes and TCP-only bytes under these methods. One can see that after enabling “P4 ad blocker,” the number of “All protocols” bytes can be reduced by 20.73% while the number of TCP-only bytes can be reduced by 20.55%.
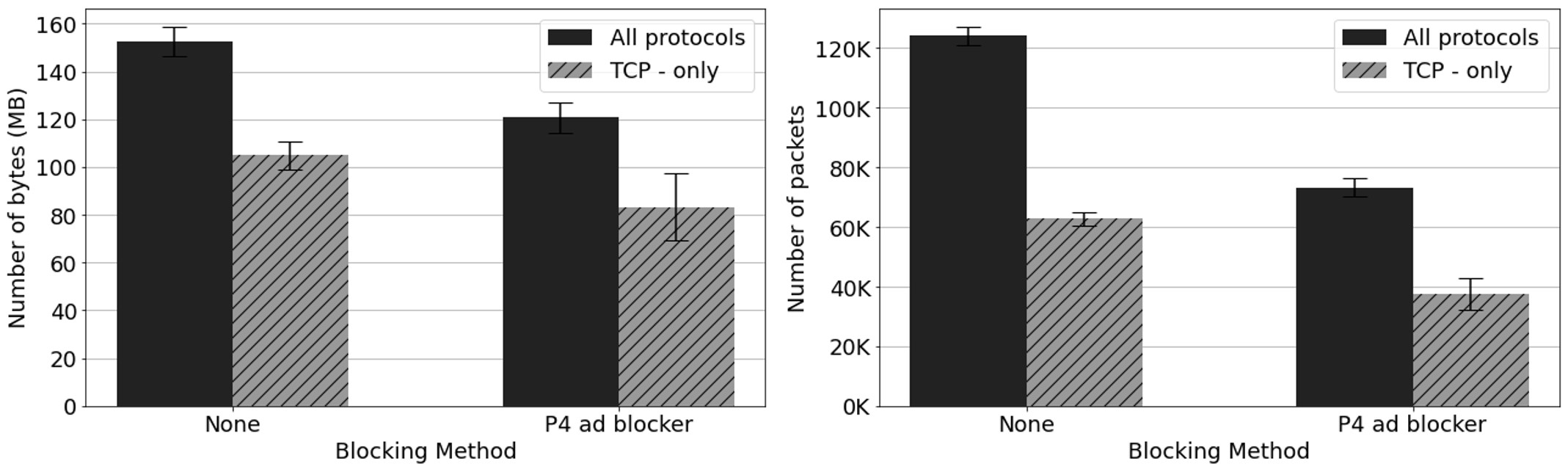
Fig. 2: P4 AD Blocker